-
Have you heard about the latest productivity update from our friends at Google? They’ve just added a little feature to Google Calendar that could make your life a whole lot easier – especially if you’re a hybrid worker. Remember back in 2021 when they first introduced the option to
-
In the fast evolving world of technology, business owners and managers like you are always on the lookout for the next big thing to give them a competitive edge. Have you considered how AI tools might be able to help? ChatGPT – or Generative Pretrained Transformer, if you want to
-
In today’s interconnected world, technology is an integral part of our daily lives, and remote workers face unique challenges when it comes to securing their home networks. A protected home network is more critical than ever, as it safeguards personal data against potential cyber threats, particularly for those working outside
-
Are you aware that the rise in global VPN usage has skyrocketed? The reasons are clear as day: Virtual Private Networks offer increased security, anonymity, and allow access to geo-restricted content online. But here’s the million-dollar question: Are all VPNs created equal? The answer is a resounding no. And that
-
It’ll come as no surprise, but Microsoft has yet more exciting news for us. Sometimes we wonder if they allow their employees to sleep! This time it’s a new browser aimed specifically at businesses: Edge for Business. The updated browser has security and productivity features that are perfect for
-
In the tech-driven world of today, the question isn’t if your business will have a data disaster, but when. From security breaches like ransomware attacks to problems with cloud storage services like Microsoft 365, there are many ways that your business data could be at risk. Small businesses are especially
-
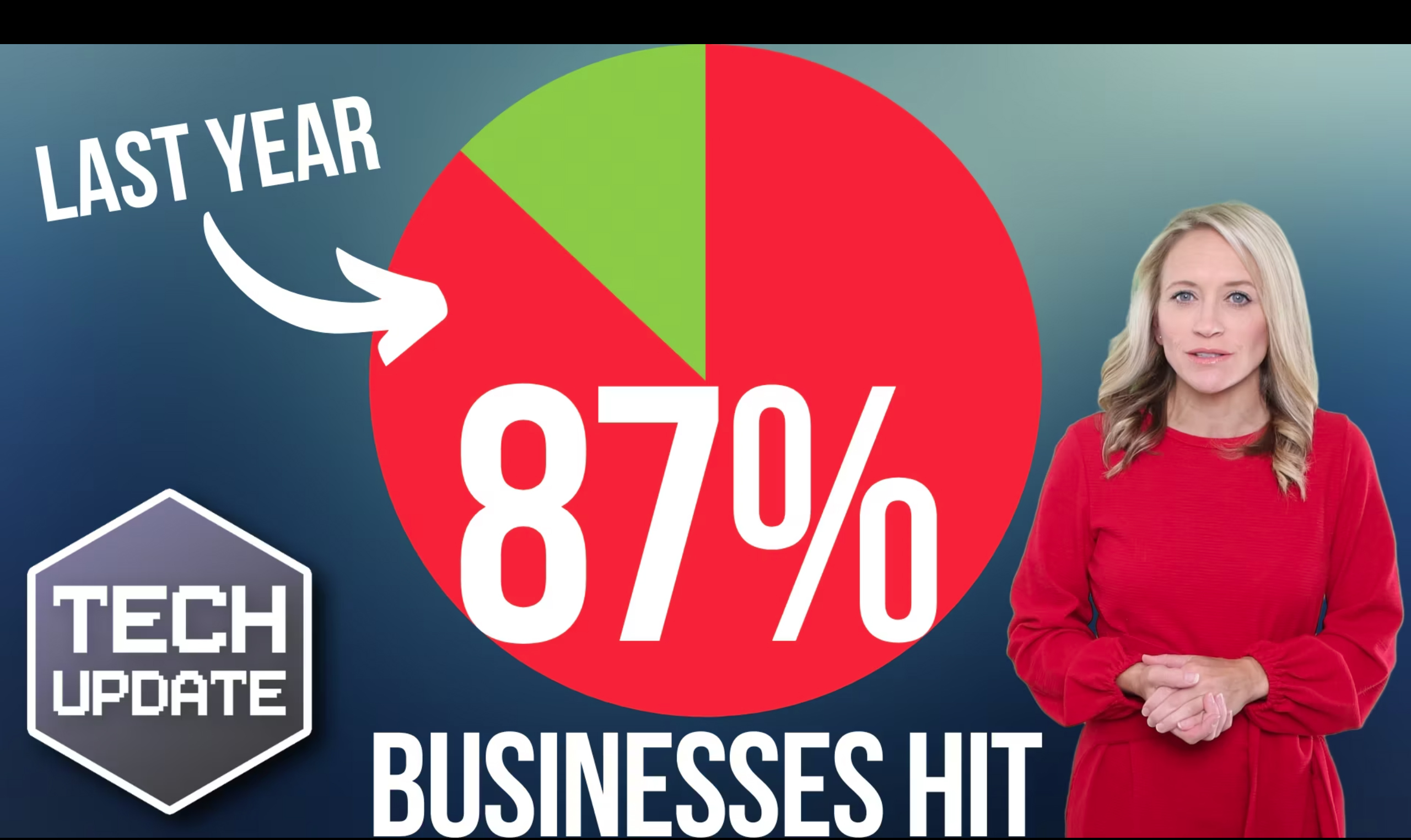
You may think that cyber attacks only happen to large corporations. But unfortunately, that’s not the case. According to a recent report, almost two-thirds of small and medium-sized businesses (SMBs) suffered at least one cyber attack over the past year. That’s a staggering number, and it should serve as a
-
The whole world is suddenly talking about Artificial Intelligence. From Alexa in your kitchen, to Siri on your phone, AI is already all around us, but new names like ChatGPT, Dall-E, Jasper and more feel like they’ve blown up the internet. These new concepts take things WAY further, helping us
910-319-7905
info@enfusetech.com